 |
| firewall |
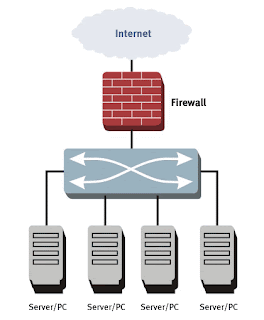
A firewall is a software or hardware device that filters the information coming through the internet. Only information that allowed by the firewall policy can go through.
There are several firewall filtering criteria:
- IP address -- a firewall can block all traffic to or from a certain IP address.
- Domain names -- a firewall can block all access to certain domain names, or allow access only to specific domain names.
- Protocols -- a firewall may set up a few hosts to handle a specific protocol and ban that protocol on other hosts.
- Ports -- a firewall can block the access of certain ports on all the hosts inside the LAN.
- Keywords -- a firewall can search through each packet for an exact match of the keywords listed in the filter.
The level of security you set for the firewall will determine how many security threats can be stopped by the firewall. Although higher level of security is more safe, it also limits your internet connectivity -- more information, useful or not, will be blocked.
The following video is a walk-through of firewall configuration with cisco SDM.
A function that is often combined with a firewall is a proxy server.
The proxy server is used to access web pages by a server acting as "middle-man". When a computer requests a web page, the proxy server retrieves the page on the behalf of that requesting computer and then sent the page to it. The net effect of this action is that the remote computer hosting the web page never comes into direct contact with the requesting computers, other than the proxy server.
 |
| proxy |
Proxy servers can also make your internet access work more efficiently by caching visited webpages on the proxy server. The next time a user visits the same webpage, the webpage will be loaded instantaneously from the proxy server, instead of retrieving again from the website.
There are times that you may want remote users to have full access to a few computers on your network such as web server or FTP server. In these cases, you may want to create a Demilitarized Zone (DMZ), which is just an area that is outside the firewall. You can create a DMZ simply by placing a few computers between the internet connection and the firewall. Most of the software firewalls available will allow you to designate a directory on the gateway computer as a DMZ.
CCENT will ask you to Describe the functions of common security appliances and applications.
Good luck for your CCENT and CCNA exam.
ICND1 and ICND2 break down
No comments:
Post a Comment