Consider The following situations:
- You have server that connected to a switch, and you want the port to shut down if a device with a different MAC addresses attempts to connect to that port.
- You have your laptop connected to a switch port in the office, and you don't want any salesman came into your office, unplug the cable from you laptop, and gain access to your switch!
To answer the above scenarios, port security shall be configured on your switch. The Cisco switch use MAC address to enforce port security. With switch port security, you can control which devices are allowed to communicate through a given switch port.
Options for configuring switch port security are:
- Identify specific MAC addresses or allow auto-learning.
- Set the maximum number of devices per port.
- Configure the action to take for unallowed devices.
Use the mac-address-table static configuration command to add static entries to the MAC address table. Use the no form of this command to remove static entries from the MAC address table.
mac-address-table static hw-addr in-port out-port-list
no mac-address-table static hw-addr
show mac-address-table
Example
The following example adds a static address with port 1 as an input port and port 2 and port 8 as output ports:
Switch(config)# mac-address-table static c2f3.220a.12f4 fa0/1 fa0/2 fa0/8
Use the switchport port-security interface configuration command to enable port security on a port. Use the no form of this command to return the interface to its default value.
command "switchport mode access" set trunking mode to ACCESS unconditionally.
command "switchport port-security" enable port security features on the interface.
command "switchport port-security maximum 10" set the maximum number of allowed devices to 10.
command "switchport port-security violation shutdown" set the action to take as shutdown when unallowed devices are attached to the switch port. The other two options are restrict and protect.
command "switchport port-security mac-address sticky" set the switch in sticky mode, so that the mac address of the firstly attached device will be used as the allowed mac address.
command "switchport port-security mac-address 0000.0000.aaaa" manually add allowed MAC address (0000.0000.aaaa) to the MAC address table.
command "no switchport port-security" set the port-security to the default value.
After the port security is configured, we can verify the status with show commands under global configuration mode.
command "show port-security" displays the port security settings for the switch.
command "show port-security interface fa 0/0" displays the port-security information for a particular interface.
command "show port-security address" displays the secure MAC address for all ports.
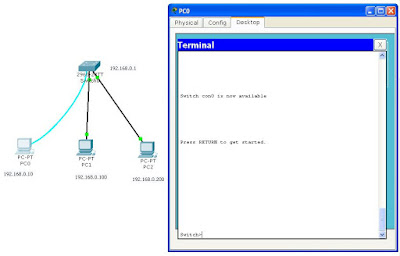
The following Demo shows how to enable port security on a switch port. The lab environment is PacketTracer5.1, the switch is 2960-24TT.
 |
| up |
As shown in the graph, the ip addresses have already been set on the switch and the 3 PCs. (If you don't remember how to do it, review basic switch commands.) PC0 is connected to the switch's console port via a console cable in order to access the CLI. PC1 and PC2 are connected to the switch's FastEthernet0/1 and FastEthernet0/2 respectively via straight-through cables.
At step 1, we first checked the MAC table with command "show mac-address-table". At the first time, There's no record in the MAC table, because they aged out. To refresh the MAC table, we sent a ping to the broadcast address of 192.168.0.255, so that the switch can learn all the MAC addresses in the broadcast domain.
At step 2, we verified the port-security status with various show command under the priviledged EXEC mode.
At step 3, we configured the port security on interface FastEthernet0/1 under interface configuration mode. The maximum number of addresses that the port can learn is set to 1. When unallowed devices are attacked to the switch port, the port will shutdown.
At step 4, we verified the port-security status with various show commands under the priviledged EXEC mode. The output shows that port-security has been correctly configured.
At step 5, we re-attached the switch's FastEthernet0/1 port from PC1 to PC2. The port-security took effect: after we refreshed the MAC table with command "ping 192.168.0.255", the port FastEthernet0/1 was down.
 |
| down |
At step 6, we verified the status of interface FastEthernet0/1 with show commands.
Switch>enable
Switch#show mac-address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
Switch#ping 192.168.0.255
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.255, timeout is 2 seconds:
Reply to request 0 from 192.168.0.100, 47 ms
Reply to request 1 from 192.168.0.100, 32 ms
Reply to request 1 from 192.168.0.200, 47 ms
Reply to request 2 from 192.168.0.200, 16 ms
Reply to request 2 from 192.168.0.100, 32 ms
Reply to request 3 from 192.168.0.200, 16 ms
Reply to request 3 from 192.168.0.100, 32 ms
Reply to request 4 from 192.168.0.200, 16 ms
Reply to request 4 from 192.168.0.100, 32 ms
Switch#show mac-address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 0040.0b6a.3b66 DYNAMIC Fa0/1
1 0050.0f68.7a19 DYNAMIC Fa0/2
Switch#show port-security
Switch#show port-security address
Secure Mac Address Table
-------------------------------------------------------------------------------
Vlan Mac Address Type Ports Remaining Age
(mins)
---- ----------- ---- ----- -------------
------------------------------------------------------------------------------
Total Addresses in System (excluding one mac per port) : 0
Max Addresses limit in System (excluding one mac per port) : 1024
Switch#show port-security interface fa0/1
Port Security : Disabled
Port Status : Secure-down
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 0
Configured MAC Addresses : 0
Sticky MAC Addresses : 0
Last Source Address:Vlan : 0000.0000.0000:0
Security Violation Count : 0
Switch#show port-security interface fa0/2
Port Security : Disabled
Port Status : Secure-down
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 0
Configured MAC Addresses : 0
Sticky MAC Addresses : 0
Last Source Address:Vlan : 0000.0000.0000:0
Security Violation Count : 0
Switch#config t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#interface fa0/1
Switch(config-if)#switchport mode access
Switch(config-if)#switchport port-security
Switch(config-if)#switchport port-security maximum 1
Switch(config-if)#switchport port-security violation shutdown
Switch(config-if)#switchport port-security mac-address sticky
Switch(config-if)#^Z
%SYS-5-CONFIG_I: Configured from console by console
Switch#show mac-address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 0050.0f68.7a19 DYNAMIC Fa0/2
Switch#ping 192.168.0.255
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.255, timeout is 2 seconds:
Reply to request 0 from 192.168.0.200, 15 ms
Reply to request 0 from 192.168.0.100, 31 ms
Reply to request 1 from 192.168.0.200, 15 ms
Reply to request 1 from 192.168.0.100, 31 ms
Reply to request 2 from 192.168.0.200, 15 ms
Reply to request 2 from 192.168.0.100, 31 ms
Reply to request 3 from 192.168.0.200, 15 ms
Reply to request 3 from 192.168.0.100, 31 ms
Reply to request 4 from 192.168.0.200, 15 ms
Reply to request 4 from 192.168.0.100, 31 ms
Switch#show mac-address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 0040.0b6a.3b66 STATIC Fa0/1
1 0050.0f68.7a19 DYNAMIC Fa0/2
Switch#show port-security
Switch#show port-security address
Secure Mac Address Table
-------------------------------------------------------------------------------
Vlan Mac Address Type Ports Remaining Age
(mins)
---- ----------- ---- ----- -------------
1 0040.0B6A.3B66 SecureSticky FastEthernet0/1 -
------------------------------------------------------------------------------
Total Addresses in System (excluding one mac per port) : 0
Max Addresses limit in System (excluding one mac per port) : 1024
Switch#show port-security interface fa0/1
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 1
Configured MAC Addresses : 0
Sticky MAC Addresses : 1
Last Source Address:Vlan : 0040.0B6A.3B66:1
Security Violation Count : 0
Switch#
%LINK-5-CHANGED: Interface FastEthernet0/1, changed state to down
%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to down
%LINK-5-CHANGED: Interface FastEthernet0/1, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to up
Switch#ping 192.168.0.255
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.0.255, timeout is 2 seconds:
Reply to request 0 from 192.168.0.200, 16 ms
%LINK-5-CHANGED: Interface FastEthernet0/1, changed state to administratively down
%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to down
Reply to request 1 from 192.168.0.200, 32 ms
Reply to request 2 from 192.168.0.200, 32 ms
Reply to request 3 from 192.168.0.200, 32 ms
Reply to request 4 from 192.168.0.200, 15 ms
Switch#show port-security address
Secure Mac Address Table
-------------------------------------------------------------------------------
Vlan Mac Address Type Ports Remaining Age
(mins)
---- ----------- ---- ----- -------------
1 0040.0B6A.3B66 SecureSticky FastEthernet0/1 -
------------------------------------------------------------------------------
Total Addresses in System (excluding one mac per port) : 0
Max Addresses limit in System (excluding one mac per port) : 1024
Switch#show port-security interface fa0/1
Port Security : Enabled
Port Status : Secure-shutdown
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 1
Configured MAC Addresses : 0
Sticky MAC Addresses : 1
Last Source Address:Vlan : 0001.6455.1023:1
Security Violation Count : 1
Switch#show interface fa0/1
FastEthernet0/1 is down, line protocol is down (err-disabled)
Hardware is Lance, address is 00e0.b0b6.ee01 (bia 00e0.b0b6.ee01)
MTU 1500 bytes, BW 100000 Kbit, DLY 1000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 100Mb/s
input flow-control is off, output flow-control is off
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:08, output 00:00:05, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue :0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
956 packets input, 193351 bytes, 0 no buffer
Received 956 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
0 watchdog, 0 multicast, 0 pause input
0 input packets with dribble condition detected
2357 packets output, 263570 bytes, 0 underruns
0 output errors, 0 collisions, 10 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier
0 output buffer failures, 0 output buffers swapped out
Switch#
Switch port security is an important topic from CCENT, to CCNA to CCNP to CCIE. After going through the above lab exercise, lets summarize it from Theoretical perspective.
ICND1 and ICND2 break down
nlce work here
ReplyDelete